[ -- Edito -- ] 0x000 - README.TXT | (English version)
January 1, 2023 edito malware
Here we are, it is September 26, 2022, and the Corbeil-Essonnes hospital has just seen 11 GB of its data published following a cyber attack by a group of criminals. These cybercriminals finally carried out their threats on the data they had encrypted AND stolen a month earlier. Hackers? Not at all: clients… Yes, clients of the Ransomware As A Service (RaaS) Lockbit: a few Bitcoins to have a Ransomware factory in SaaS mode.
The number of healthcare institutions affected by these disgusting and abject attacks called RANSOMWARE is countless.
I was born in the 70s, APPLE IIC in 1983, Linux in 1994, AWS since 2008, I am what the industry calls an Ethical Hacker. I have spent the last twenty years imagining, designing, coding, and auditing applications, systems, platforms, and clouds. BBS in RTC, UUCP, then the Web (1.0, 2.0, and today 3.0), I have embraced the technological innovations of the internet with personal passion and economic entrepreneurship.
MALWARE, RANSOMWARE for novices are computer ailments, for victims, it is a digital nightmare, for developers, CIOs, CISOs, and many people in security, they are horrible programs to be protected against: by prevention for users on the one hand and by implementing the right software solutions (e.g., XDR) on the other hand.
For an Ethical Hacker, Malware is code to reverse to understand, learn with the aim of fighting this modern scourge: a mystery to dig into: REVERSE ENGINEERING, the queen discipline of security, consists of analyzing the code and behaviors of a program for which we do not have the source code. This definition is not quite accurate, because for a hacker: we always have the source code, it is just expressed in a language and patterns that at first glance may seem a bit stiff: the architecture of X86 and ARM microprocessors and their respective assemblers.
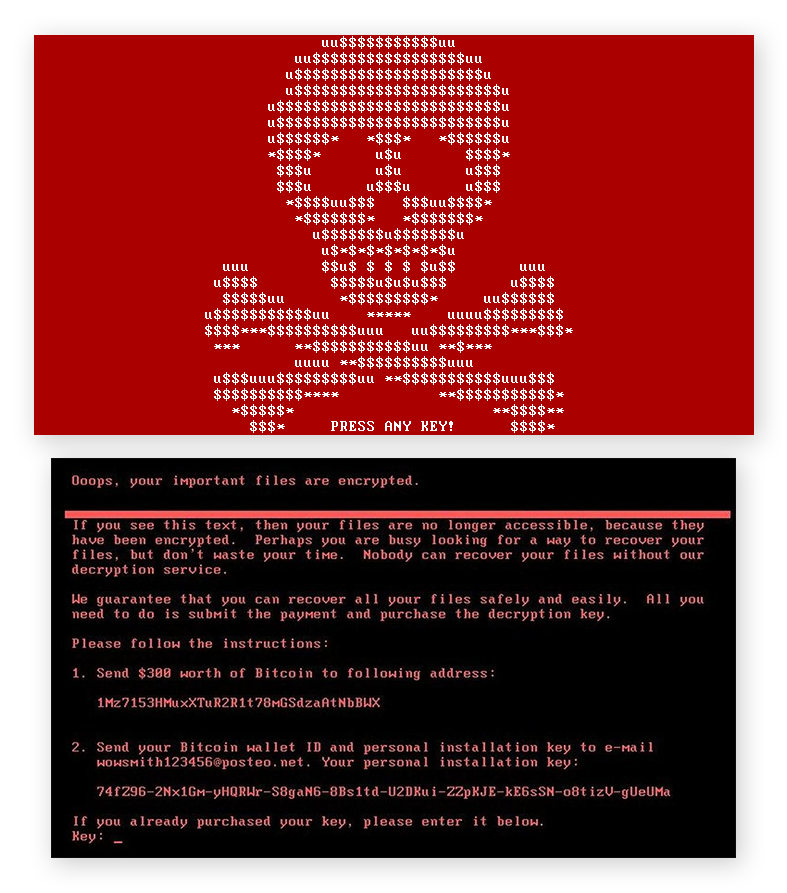
So, you may have understood, following the event at the Corbeil-Essonnes Hospital, I am opening this blog today to contribute a small stone to the dissemination of knowledge in Reverse Engineering. I choose to do it in French because this subject is little covered (although it is fascinating), because I am a lover of French literature and because I am fed up with hearing only about American, Russian, Chinese, and Korean hackers.
Obviously, those who follow all this more closely know well that we have entered into a war and that we must mobilize all the living forces of our beautiful country and Europe to avoid a digital Blitzkrieg.
Cracking WIFI passwords, Windows Hashes, or other nonsense of this kind will find no echo here: there are enough sites to make you think you are a hacker with KALI and a few GPUs, or better, to start a career as a WEB Pentester. No, here we will reverse code and programs and files (often binaries), decrypt assembler, do a bit of cryptography, and conduct digital investigations. Our goal is to learn to reverse programs, then increasingly complex malware. We can only fight effectively what we understand in depth, so let’s start with understanding.
_NaPtaX – In tribute to Aaron Swartz –